Data Physics
The Semantic Capture of Intent
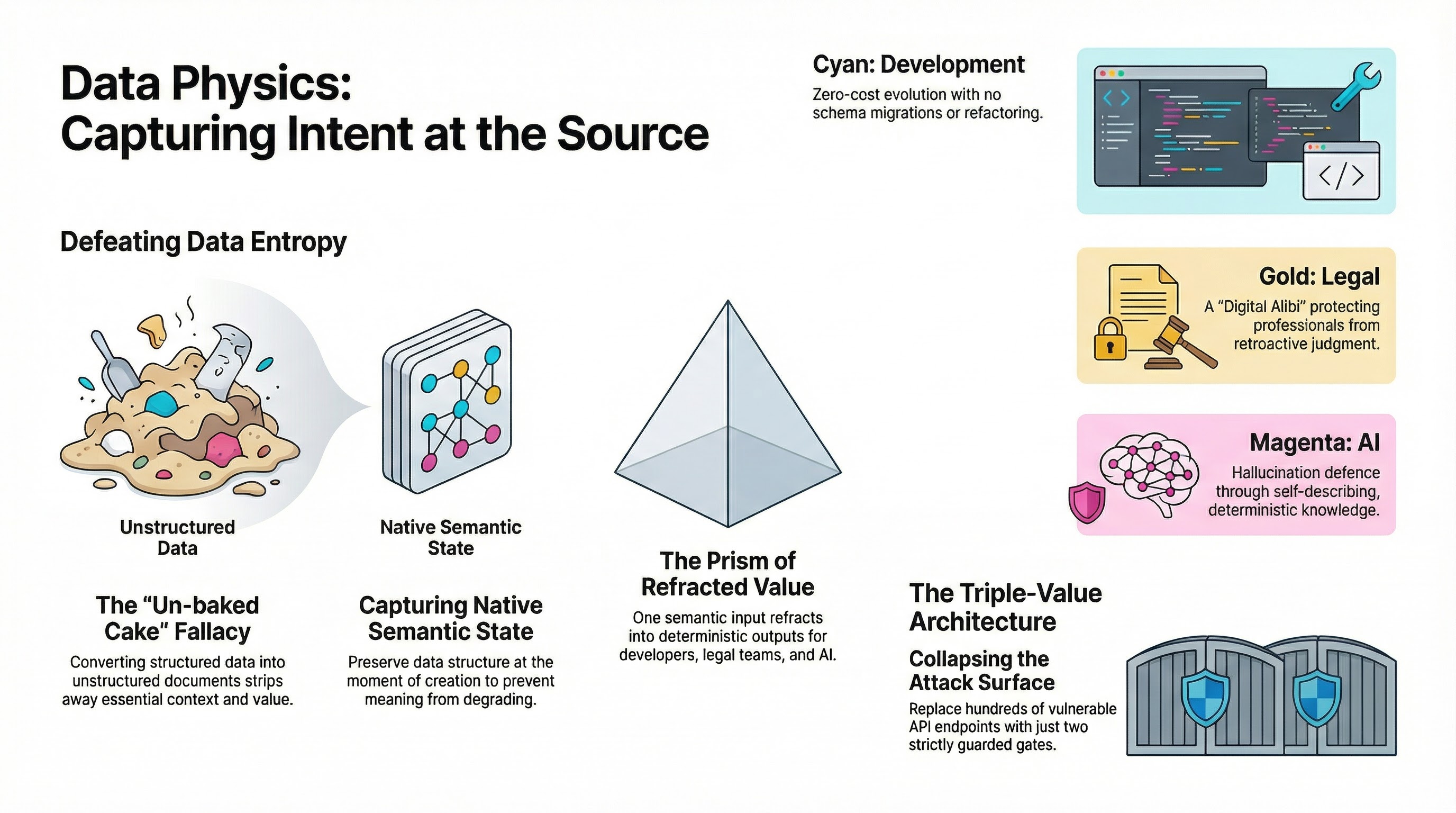
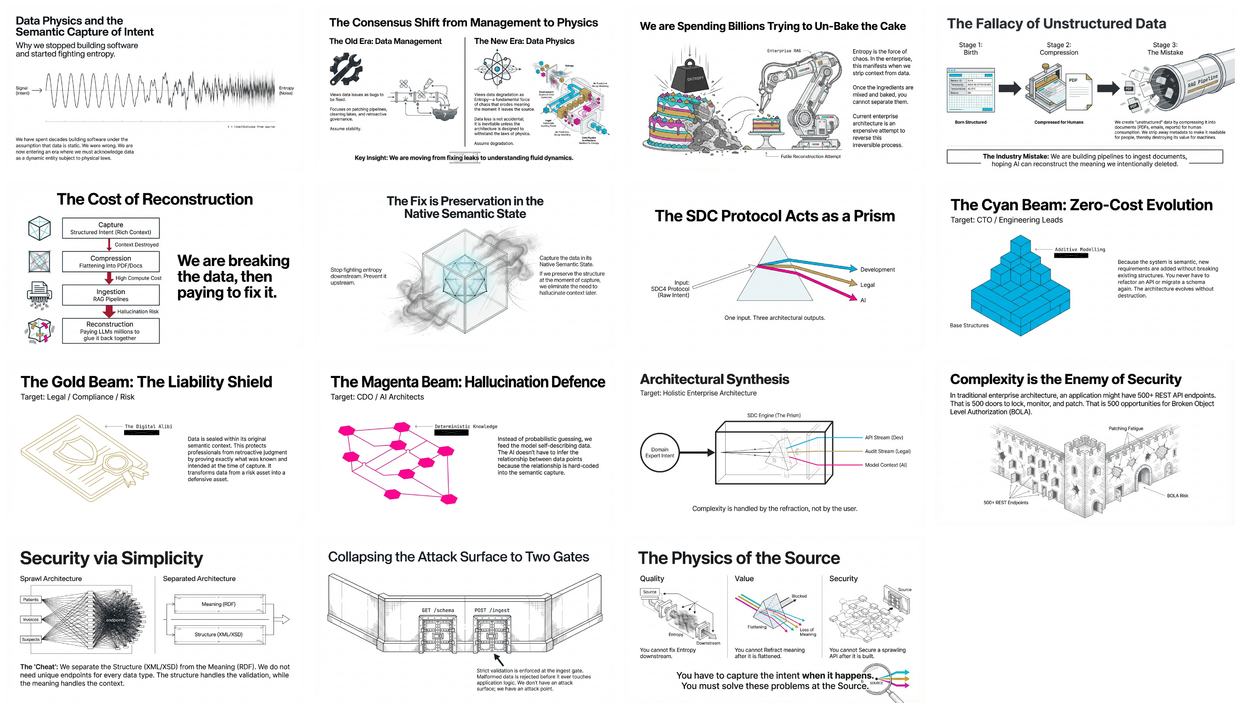
The “Data Management” era is over. The “Data Physics” era has begun. We now realize that data issues are not bugs to fix — they are entropy, a fundamental force of chaos that degrades meaning the moment it leaves the source. Three metaphors frame the SDC approach: The Cake, The Prism, and The Fortress.
Content by: Dinis Cruz — Licensed under Creative Commons Attribution 4.0 International (CC BY 4.0). Based on a Substack post by Timothy Cook.
The Three Metaphors
Key Concepts
Data Physics
A paradigm shift from “Data Management” — treating data degradation as entropy, a fundamental force of chaos requiring prevention rather than repair.
Data Entropy
The degradation of meaning that occurs the moment data leaves its source — structure and context are progressively lost.
Native Semantic State
Capturing data with its full structure and metadata at the moment of creation, before entropy destroys its machine-readable value.
SDC4 Protocol
The Semantic Data Charter protocol acting as “white light” — raw domain expert intent that refracts into development, legal, and AI value streams.
Core Arguments
Data is born structured — form entries, sensor readings, transactions all start with structure. We compress them into documents for human readability, destroying their machine value.
RAG is expensive reconstruction — we are paying billions to LLM companies to reconstruct context we deliberately destroyed when flattening data into PDFs and reports.
Solve at source, not downstream — you cannot secure a sprawling API after it’s built, govern data after it’s flattened, or fix context after the domain expert has retired.
Security through simplicity — 500 REST endpoints means 500 BOLA attack vectors; collapsing to 2 well-guarded gates with strict validation eliminates the attack surface.
Single source, multiple outputs — the SDC4 Protocol captures intent once and produces development (zero-cost evolution), legal (liability shield), and AI (hallucination defense) value.
Key Quotes
Semantic Knowledge Graph
Machine-readable metadata for search, discovery, and graph database integration.
The Entropy Problem vs Solution
flowchart TD
subgraph Problem["Current State: Data Entropy"]
A[Structured Data Born] --> B[Compressed to Documents]
B --> C[Context Destroyed]
C --> D[RAG Pipeline]
D --> E[LLM Reconstruction]
E --> F[Hallucinated Context]
end
subgraph Solution["Data Physics: Semantic Capture"]
G[Domain Expert Intent] --> H[SDC4 Protocol]
H --> I[Native Semantic State]
I --> J[Preserved Structure]
J --> K[Zero Entropy]
end
Problem -.->|"Billions $ Spent"| F
Solution -.->|"Prevent at Source"| K
style Problem fill:#ffcdd2,stroke:#c62828
style Solution fill:#c8e6c9,stroke:#2e7d32
Value Prism Architecture
flowchart LR
subgraph input ["INPUT"]
WHITE["White Light\nDomain Expert Intent"]
end
subgraph prism ["SDC4 PRISM"]
SDC["Semantic Data\nCharter"]
end
subgraph outputs ["VALUE BEAMS"]
CYAN["Cyan Beam\nDevelopment\nZero-Cost Evolution"]
GOLD["Gold Beam\nLegal\nLiability Shield"]
MAGENTA["Magenta Beam\nAI\nHallucination Defense"]
end
WHITE --> SDC
SDC --> CYAN
SDC --> GOLD
SDC --> MAGENTA
style input fill:#fff9c4,stroke:#f9a825
style prism fill:#e1bee7,stroke:#7b1fa2
style CYAN fill:#b2ebf2,stroke:#00838f
style GOLD fill:#ffe082,stroke:#ff8f00
style MAGENTA fill:#f8bbd9,stroke:#c2185b
Security Architecture: The Fortress
graph TB
subgraph Traditional["Traditional: 500 Attack Vectors"]
E1["/patients"]
E2["/invoices"]
E3["/suspects"]
E4["/orders"]
E5["... 496 more"]
ATK1((Attacker))
ATK1 -.->|"BOLA"| E1
ATK1 -.->|"BOLA"| E2
ATK1 -.->|"BOLA"| E3
end
subgraph SDCArch["SDC: 2 Guarded Gates"]
G1["GET /schema\nHere is the map"]
G2["POST /ingest\nHere is the payload"]
V[Strict Validation]
G2 --> V
V -->|Valid| App[Application Logic]
V -->|Invalid| Reject[Reject Before Processing]
ATK2((Attacker))
ATK2 -.->|"Blocked"| V
end
style Traditional fill:#ffcdd2,stroke:#c62828
style SDCArch fill:#c8e6c9,stroke:#2e7d32
Complete Knowledge Graph
graph TB
subgraph paradigms ["Paradigms"]
DP["Data Physics\n(paradigm)"]
DM["Data Management\n(paradigm, obsolete)"]
end
subgraph concepts ["Concepts"]
ENT["Data Entropy\n(concept)"]
NSS["Native Semantic State\n(concept)"]
end
subgraph metaphors ["Metaphors"]
CAKE["The Cake\n(metaphor)"]
PRISM["The Prism\n(metaphor)"]
FORT["The Fortress\n(metaphor)"]
end
subgraph technologies ["Technologies"]
SDC["SDC4 Protocol\n(technology)"]
GETS["GET /schema\n(technology)"]
POST["POST /ingest\n(technology)"]
end
subgraph values ["Value Streams"]
CYAN["Cyan: Development\n(value_stream)"]
GOLD["Gold: Legal\n(value_stream)"]
MAG["Magenta: AI\n(value_stream)"]
end
subgraph problems ["Problems"]
RAG["RAG Costs\n(problem)"]
BOLA["BOLA Attacks\n(problem)"]
end
DP -->|replaces| DM
DP -->|addresses| ENT
NSS -->|prevents| ENT
SDC -->|captures| NSS
CAKE -->|frames| RAG
PRISM -->|frames| SDC
FORT -->|frames| BOLA
SDC -->|produces| CYAN
SDC -->|produces| GOLD
SDC -->|produces| MAG
FORT -->|implements| GETS
FORT -->|implements| POST
CAKE -->|solves| RAG
FORT -->|solves| BOLA
style DP fill:#c8e6c9,stroke:#2e7d32
style DM fill:#ffcdd2,stroke:#c62828
style ENT fill:#ffecb3,stroke:#ff8f00
style NSS fill:#b2ebf2,stroke:#00838f
style CAKE fill:#f3e5f5,stroke:#7b1fa2
style PRISM fill:#f3e5f5,stroke:#7b1fa2
style FORT fill:#f3e5f5,stroke:#7b1fa2
style SDC fill:#e3f2fd,stroke:#1565c0
style CYAN fill:#b2ebf2,stroke:#00838f
style GOLD fill:#ffe082,stroke:#ff8f00
style MAG fill:#f8bbd9,stroke:#c2185b
style RAG fill:#ffcdd2,stroke:#c62828
style BOLA fill:#ffcdd2,stroke:#c62828
Taxonomy
data_physics_domain
├── paradigms
│ ├── data_physics
│ │ ├── entropy_as_force
│ │ └── solve_at_source
│ └── data_management (obsolete)
│ ├── bugs_to_fix
│ └── downstream_repair
├── concepts
│ ├── data_entropy
│ ├── native_semantic_state
│ └── intent_capture
├── metaphors
│ ├── the_cake
│ │ ├── born_structured
│ │ ├── compressed_for_humans
│ │ └── unbaking_expensive
│ ├── the_prism
│ │ ├── white_light_intent
│ │ └── refracted_value
│ └── the_fortress
│ ├── attack_surface_reduction
│ └── validation_at_gate
├── technologies
│ ├── sdc4_protocol
│ ├── get_schema_endpoint
│ └── post_ingest_endpoint
├── value_streams
│ ├── cyan_development
│ ├── gold_legal
│ └── magenta_ai
└── problems
├── rag_reconstruction_costs
├── bola_attacks
└── context_loss
Neo4j Graph Import
Import this knowledge graph into Neo4j to explore the Data Physics domain interactively.
Cypher Import Script
// Data Physics Domain - Neo4j Import
// Create Paradigm nodes
CREATE (dp:Paradigm {id: 'data_physics', name: 'Data Physics',
description: 'Treating data management as physics with entropy as fundamental force'})
CREATE (dm:Paradigm {id: 'data_management', name: 'Data Management',
description: 'Traditional approach treating data issues as bugs', status: 'obsolete'})
// Create Concept nodes
CREATE (entropy:Concept {id: 'data_entropy', name: 'Data Entropy',
definition: 'Degradation of meaning as data moves from source'})
CREATE (nss:Concept {id: 'native_semantic_state', name: 'Native Semantic State',
definition: 'Data captured with full structure at creation'})
// Create Metaphor nodes
CREATE (cake:Metaphor {id: 'the_cake', name: 'The Cake',
problem: 'Un-baking compressed documents', solution: 'Capture at source'})
CREATE (prism:Metaphor {id: 'the_prism', name: 'The Prism',
problem: 'Multiple value streams needed', solution: 'Single source refracts'})
CREATE (fortress:Metaphor {id: 'the_fortress', name: 'The Fortress',
problem: '500+ attack vectors', solution: '2 guarded gates'})
// Create Technology nodes
CREATE (sdc:Technology {id: 'sdc4_protocol', name: 'SDC4 Protocol',
purpose: 'Semantic Data Charter for intent capture'})
CREATE (getSchema:Technology {id: 'get_schema', name: 'GET /schema',
purpose: 'Provide the data map'})
CREATE (postIngest:Technology {id: 'post_ingest', name: 'POST /ingest',
purpose: 'Accept payload with validation'})
// Create ValueStream nodes
CREATE (cyan:ValueStream {id: 'cyan_beam', name: 'Cyan Beam',
target: 'Development', benefit: 'Zero-Cost Evolution'})
CREATE (gold:ValueStream {id: 'gold_beam', name: 'Gold Beam',
target: 'Legal', benefit: 'Liability Shield'})
CREATE (magenta:ValueStream {id: 'magenta_beam', name: 'Magenta Beam',
target: 'AI', benefit: 'Hallucination Defense'})
// Create Problem nodes
CREATE (rag:Problem {id: 'rag_costs', name: 'RAG Reconstruction Costs',
cost: 'Billions', description: 'Paying LLMs to reconstruct destroyed context'})
CREATE (bola:Problem {id: 'bola_attacks', name: 'BOLA Attacks',
risk: 'High', description: 'Broken Object Level Authorization on many endpoints'})
// Create Person node
CREATE (dc:Person {id: 'dinis_cruz', name: 'Dinis Cruz', role: 'Security Researcher'})
// Create Relationships
CREATE (dp)-[:REPLACES]->(dm)
CREATE (dp)-[:ADDRESSES]->(entropy)
CREATE (nss)-[:PREVENTS]->(entropy)
CREATE (sdc)-[:CAPTURES]->(nss)
CREATE (cake)-[:FRAMES]->(rag)
CREATE (prism)-[:FRAMES]->(sdc)
CREATE (fortress)-[:FRAMES]->(bola)
CREATE (sdc)-[:PRODUCES]->(cyan)
CREATE (sdc)-[:PRODUCES]->(gold)
CREATE (sdc)-[:PRODUCES]->(magenta)
CREATE (fortress)-[:IMPLEMENTS]->(getSchema)
CREATE (fortress)-[:IMPLEMENTS]->(postIngest)
CREATE (cake)-[:SOLVES]->(rag)
CREATE (fortress)-[:SOLVES]->(bola)
CREATE (fortress)-[:REFERENCES]->(dc)
How to use this in Neo4j
- Create a free Neo4j Sandbox at sandbox.neo4j.com — select “Blank Sandbox”
- Open Neo4j Browser and paste the Cypher code above into the query editor
- Run the query (click the play button or press Ctrl+Enter)
- Visualize the graph with:
MATCH p=()-[]-() RETURN p
Tags
Source Information
| Original Author | Timothy Cook |
| Original Post | Substack |
| Content Created By | Dinis Cruz |
| License | CC BY 4.0 International |
| Generated With | Google NotebookLM |
| Format | PDF (15 slides) + Infographic |
| Date | January 2026 |
Continue Reading
Explore the foundational thesis about Data Entropy and the case for native semantic capture.